 SIEM vs. SOAR vs. XDR:
SIEM vs. SOAR vs. XDR:

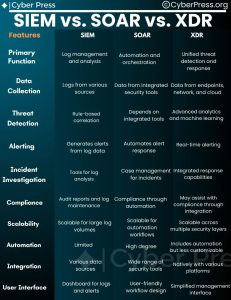
Understanding the Key Differences and How They Work Together in today’s rapidly evolving cybersecurity landscape, organizations need robust tools to detect, respond to, and mitigate threats. Three of the most significant technologies in this space are SIEM, SOAR, and XDR. While each serves a unique purpose, they often complement each other in creating a more secure environment.1. SIEM (Security Information and Event Management)Primary Function: SIEM solutions are designed to collect, analyze, and correlate security events and log data from various sources within an organization’s IT infrastructure. They provide real-time visibility into potential security incidents and help identify patterns that could indicate a threat.Example Products:SplunkIBM QRadarArcSightHow It Works: SIEM systems aggregate data from firewalls, antivirus programs, servers, applications, and other devices, then analyze this data for unusual patterns or anomalies. The system generates alerts that security teams can investigate further. SIEM is particularly useful for compliance reporting and providing a centralized view of security events across an organization.2. SOAR (Security Orchestration, Automation, and Response)Primary Function: SOAR platforms are designed to automate and coordinate security operations processes, helping security teams manage and respond to incidents more effectively and efficiently. These tools reduce the manual effort involved in responding to threats, allowing teams to focus on more complex tasks.Example Products:Palo Alto Networks Cortex XSOARSplunk SOAR (formerly Phantom)IBM ResilientHow It Works: SOAR platforms integrate with various security tools (including SIEMs) and automate workflows for incident response. For example, when a SIEM generates an alert, a SOAR platform can automatically trigger a predefined response action, such as isolating a compromised device or blocking malicious IP addresses. SOAR solutions also provide case management, threat intelligence, and collaboration tools, enhancing the overall effectiveness of security operations.3. XDR (Extended Detection and Response)Primary Function: XDR is an advanced security solution that goes beyond traditional endpoint detection and response (EDR) by integrating data from multiple security layers—such as endpoint, network, and email—to provide a unified and comprehensive threat detection and response platform.Example Products:Palo Alto Networks Cortex XDRTrend Micro XDRMicrosoft Defender XDRHow It Works: XDR solutions collect and correlate data from various security tools across the entire environment, providing deeper visibility and more accurate threat detection. By breaking down silos between different security layers, XDR offers a more holistic view of security incidents and automates response actions across all affected systems. This integration leads to faster detection and more coordinated responses to threats.Key Differences:SIEM focuses on log aggregation and analysis to identify potential security incidents and is widely used for compliance and reporting.SOAR emphasizes automation and orchestration of security operations, helping teams respond to incidents faster and with fewer manual processes.XDR provides comprehensive detection and response across multiple security layers, offering a more integrated approach to threat management compared to traditional EDR solutions.How They Work Together:SIEM can be used to feed data into SOAR platforms, which then automate the response to the alerts generated by the SIEM. This combination improves the speed and efficiency of threat response.XDR solutions can complement SIEM by providing more context and correlation across different security layers, enhancing the detection capabilities. When integrated with a SOAR platform, XDR can automate responses based on enriched data, creating a powerful defense mechanism.In summary, while SIEM, SOAR, and XDR serve distinct functions, they are most effective when used together. SIEM provides the visibility, SOAR automates the response, and XDR offers an integrated, context-rich threat detection capability. By combining these technologies, organizations can significantly enhance their security posture and respond more effectively to the ever-growing landscape of cyber threats

