TheMadAdmin Cyber Security
SIEM vs. SOAR vs. XDR
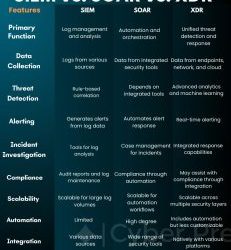
SIEM vs. SOAR vs. XDR: Understanding the Key Differences and How They Work Together in today’s rapidly evolving cybersecurity landscape, organizations need robust tools to detect, respond to, and mitigate threats. Three of the most significant technologies in this...
Learning Cyber Security
As an experienced cyber security professional, I can offer some valuable guidance on where to begin your journey. ## 1. **Understanding the Basics** - **CompTIA Security+**: This is an excellent starting point. It's a well-recognized certification that...
Top Three Cybersecurity Best Practices References
Top Three Cybersecurity Best Practices References 1. National Institute of Standards and Technology (NIST) Cybersecurity Framework Reputation: Highly respected and widely adopted within the industry, particularly in the United States. NIST is a federal agency known...
Are Your Employees Enabling External Threats?
Navigating Insider Risks: Are Your Employees Enabling External Threats? Insider risks can arise from both malicious and accidental actions by employees. Accidental insiders often compromise security due to a lack of awareness, pressure to perform, poor...
6 Types of Application Security Testing You Must Know About
Friendly Summary by TheMadAdmin (AKA Dave) 6 Types of Application Security Testing You Must Know About Application security testing is essential for developing secure software. Here are six key types: Penetration Testing for the SDLC: Identifies vulnerabilities...
North Korean Hackers Shift from Cyber Espionage to Ransomware Attacks
\ North Korean Hackers Shift from Cyber Espionage to Ransomware Attacks North Korean hackers, specifically the group APT45, known for cyber espionage, are now focusing on ransomware attacks. Google-owned Mandiant reports that APT45 has targeted critical infrastructure...