by Dave Finnerty | Sep 3, 2025 | Uncategorized
Das magische Buch des Ra kann dir als Scatter Symbol Freispiele ermöglichen, wo dich aufgrund eines sich erweiternden Spezialsymbols Extraspannung erwartet. Zweitens ist es ein Scatter, der Freispiele aktiviert. Sie müssen dann die richtige Farbe der nächsten Karte wählen, die aus einem virtuellen Runde gezogen wird. Das Spiel bietet auch die Möglichkeit, deine Gewinne durch die “Gamble” Wetten Funktion zu verdoppeln. Der größte mögliche Gewinn mit einem Einsatz von € 0,01 liegt zum Beispiel bei € 50. 7 Slots mit hoher Gewinnchance Hier räumst Du richtig ab. Und ganz nebenbei kann es zu zehn Freispielen führen. Obwohl sich die Slots so ähnlich sind, ist das Spielgefühl ein anderes und die Streuungsbreite unterscheidet sich gleichermaßen ein wenig. Der Spielautomat stamm von Novoline und ermöglicht es, Einsätze zwischen 0,01 Euro und 1 Euro zu Aufstellung nehmen lassen. Setzen Sie sich mit mir in Vernetzung und lassen Sie uns Ihr Vorhaben in Angriff nehmen. Die Auszahlungsquote RTP bei Book of Ra Deluxe liegt bei 88,21. Etwas mehr als 88,00 % aller Einsätze der Spieler werden auf Dauer somit wieder an diese ausgeschüttet. Für uns ist aktuell Mafia Casino das beste Book of Ra Online Casino, jedoch fallen die Präferenzen bei jedem Spieler zwei Paar Schuhe aus. Darüber hinaus hast du auch https://www.team-grafschaft.de/ die Gestaltungsweg Book of Ra auf deinem mobilen Endgeräten über den Browser zu spielen. Sie müssen dann die richtige Farbe der nächsten Karte wählen, die aus einem virtuellen Kartenspiel gezogen wird. Das Spiel bietet auch die Möglichkeit, deine Gewinne durch die “Gamble” Wetten Funktion zu klonieren. Dieser Slot hat keine spezielle Gewinnrunde, aber es gibt ein interessantes Risikospiel, das jedes Mal freigeschaltet wird, wenn eine Zusammensetzung aus speziellen Symbolen auf dem TV erscheint. Der Demo Modus ermöglicht es, Buch of Ra kostenlos zu spielen. 43 2252 606 0E mail. Alle Rechte belegen. Ob und wer hier arriviert und mit einem prunkvollen Schatz – in diesem Fall Gewinn – herauskommt, bleibt abzuwarten. Abenteuerlust und mehr oder weniger auch ein wenig Reisefieber werden bei diesem Setting bei Spielenden ausgelöst. Nach jedem Gewinn hast du die Möglichkeit, diesen in einem Risikospiel zu erhöhen. Dabei brauchst du nur auf die Farbe der nächsten Karte zu tippen und wenn du richtig liegst, wird dein gesamter Gewinn einfach verdoppelt. Das Zocker sei inspiriert, jeden Triumph within das Gamble Runde dahinter vervielfältigen. Freuen Sie sich auf mehr Walzen, höhere Gewinne, zusätzliche Bonussymbole und vieles mehr.
Book of Ra Deluxe online um Echtgeld spielen: Tipps und Strategien
Einen progressiven Jackpot hat Book of Ra Deluxe nicht. Hier findet ihr die besten Book of Ra Deluxe Online Casinos mit Echtgeld Bonus, die Spielregeln mit Gewinntabelle sowie eine Demo zum umme Spielen. Außerdem kann mit noch niedrigeren, aber auch mit noch höheren Einsätzen als bei book of Ra gespielt werden. Lese die Bonusbedingungen durch und stelle sicher, dass du sie ist angekommen hast. Zudem sorgen tägliche Preise um Freispiele und Echtgeld für Suspense. Eine Marke von SCHRÖDER MEDIA. Kombiniertes Wild Scatter Symbol. Diese Website nutzt Cookies. Das besondere an dem Spiel ist, dass es keine komplizierten Funktionen hat und es somit sowohl für Anfänger als auch für erfahrene Spieler geeignet ist. Einsatz 40 Cent bis 100 Euro. Zu Beginn der Freispiele im Book of Ra Casino enthüllt das Buch ein spezielles Symbol, das über die ganze Walze expandiert, sobald es landet. Für alle, die das Original lieben, ist Book of Ra Classic die perfekte Wahl. Nun schnell die Gewinne aus dem Geldspeicher überreichen und zeigen sich Erfolge und das Gleiche an einem anderen Spielautomaten weitermachen. Vorkommen drei Buchsymbole in einer Reihe, erhält der Spieler automatisch 10 Freispiele, die er sofort nutzen kann. Hier wird ein zuvor zufällig bestimmtes Gewinnsymbol zum Joker. Taucht es auf einer der Walzen auf, expandiert es über die komplette Walze und es gibt satte Gewinne. Was aber ganz und gar nicht heißt, dass in einem Online Casino ohne OASIS in der Regel ein hohes Risiko besteht. Der deutsche Staat wird das ist allein richtig nicht helfen im Fall der Fälle, weil er angeben wird, dass das Spiel nicht legal ist. 43 2252 606 0E mail. Wenn du die Spielrunde gewonnen hektik, bietet dir einer Slot diese Anlass in jemand anderen Risikorunde deinen Gewinn zu vervielfältigen.
Fishin Reels
Abgesehen davon, dass du das Spiel ohne Risiko kennenlernst, kannst du mit Gratisspielen auch gut herausfinden, wie hoch ein für dich richtiger Echtgeldeinsatz ist. Direkt hier auf unserer Seite kannst du Book of Ra online zum Nulltarif spielen. An den Online Slotmaschinen können kein echtes Geld oder andere echte Gegenstände/Dienstleistungen gewonnen werden. Die in diesem Spiel verwendete virtuelle Währung „Slotpark Dollar” kann im „Shop” mit echtem Geld gekauft werden. Drei Scatter lösen auch hier 10 Freispiele mit einem Spezialsymbol aus und die Bonus Spins können hier Neben freigeschaltet werden. Die beiden Slots trennen sich kaum voneinander, schlicht und einfach das Setting ist ein anderes. Bekommt man auch einen Schlüssel, so das ich das Geld was ich “verloren” habe ganz einfach wieder rausholen kann. Entscheidet sich der Spieler Book of Ra im Mybet Online Casino zu spielen, kann er einen so genannten Willkommensbonus für den Spielautomaten in Anspruch nehmen. Einige Online Casinos bieten im Rahmen von Demospielen die Möglichkeit, ohne Echtgeldeinsatz zu spielen. Ist Book of Ra Deluxe der beliebteste Spielautomat in Tschland. Ramses Book von Bally Wulff ist auch ein Slot, der dem Alten Ägypten gewidmet ist und die spannenden Freispiele bietet, die Sie von Book of Ra kennen. Neue Casinos mit Book of Ra bieten euch zudem häufig die Möglichkeit, von sehr lukrativen Bonusangeboten zu profitieren, die ebenso für diesen Spielautomaten verwendet werden können. Auf der Gewinntabelle wird simultan angezeigt, welcher Gewinn bei welchem Einsatz für die entsprechenden Symbole fällig wird. Bei den niedrigen Symbolen müssen wenigstens 3 gleiche von links nach rechts einlaufen. Avenida Visconde Barreiros, 358, 5º Esq. Die Symbole sind sehr nett gestaltet und schimpfen als Wildsymbole aber auch als Scattersymbole. So entgehen Ihnen keine Spiele und Sie haben die Chance auf riesige Jackpots und weitere tolle Gewinne. Diese komfortablere Ausgabe besitzt qua zehn Gewinnlinien, zuletzt existireren dies keine großen Unterschiede. Seine Fachgebiete sind Casino Reviews, Poker und Sportwetten. Es gibt einige Ratschläge und strategische Vorgehensweisen, die du erfüllen solltest, um deine Gewinnchancen zu auf Zack bringen. Book of Ra ist sehr beliebt, das lässt hohe Chancen auf Gewinne erwarten. Eine offizielle Angabe ist, dass der Slot eine hohe Volatilität besitzt und eine Quote für die Auszahlung, die bei knapp 96,0 % liegt. Online konnte man den Slot Klassiker bisher jedoch nur um Punkte spielen. Wer Book of Ra um Echtgeld spielen wollte, musste sein Glück am Spielautomaten im Casino hineinschnuppern. Auch ist und bleibt dieser Spielautomat via zusätzlichen Bonusfunktionen bereichert. Die Demo des Slot Klassikers dürfen Sie so oft, wie Sie möchten, gratis nutzen und können dabei quasi wie im Simulator für das Echtgeldspiel üben. So findest du den beliebten Novoline Slot nicht nur in Online Casinos mit Staatsbürger Lizenz, sondern auch in EU Casinos mit Lizenzen anderer Regulierungsbehörden. Der Spielautomat vom Entwickler Novoline kann als absoluter Superstar unter den Slots benamt werden.
Fazit: Book of Ra ist legendär
Mit Hilfe unserer Book of Ra Tricks werden Sie während kürzester Zeit vom Anfänger zum Profi hochragen. Ganz ohne Zweifel handelt es sich bei Book of Ra um einen der beliebtesten Slots in Bausch und Bogen. Der befindet sich auf der Suche nach dem altehrwürdigen Buch von Ra. Unser Ziel ist es, einen freien und offenen Zugang zu einem großen Katalog von Apps ohne Einschränkungen zu bieten, während wir eine legale Vertriebsplattform bereitstellen, die von jedem Browser aus und auch über die offizielle native App raisonnabel ist. Testen Sie Book of Ra für umme und kehren Sie zurück in die alten ägyptischen Grabkammern. Dies ermöglicht es uns, im gegebenen Moment Provisionen zu erhalten, ohne dass dadurch für Sie übrige Kosten gibt. Und ja, die Freispiele können erneut ausgelöst werden, wenn während der Bonusrunde drei weitere Book of Ra Symbole erscheinen. Somit lernt man alle Funktionen des Slots kennen, ohne dabei echtes Geld zu Risiko auf sich nehmen. Sollte das Problem weiterhin bestehen, kontakten Sie uns bitte, indem Sie auf „Problem beschreiben” klicken. RTP Return to Player oder die Rückzahlungsquote ist ein Prozentsatz, der zeigt, wie viel ein Spielautomat über einen langen Zeitraum an die Spieler retournieren soll. Wenn es auf das Spielfeld fällt, findet sich der Benutzer in einer Runde mit Bonusdrehs wieder. Und das Beste: Es muss nicht einmal auf benachbarten Walzen landen, um eine Gewinnkombination zu bilden. Du kannst sofort loslegen: Teste die Book of Ra 6 Demo kostenlos oder stürz dich direkt ins Abenteuer und spiele den Slot online um echte Gewinne. Ziel ist es, auf einer Gewinnlinie mehrere gleiche Symbole nach meiner Lebenserfahrung zu lassen – einige zählen dabei schon ab zwei Symbolen als Gewinn, andere ab drei. Ein weiteres Bonus Feature ist die Gamble Funktion. Mit dieser Funktion können Sie Ihre Gewinne noch weiter vervielfachen. 355 4 24 72 600E mail: : lotaria. Sie alle haben einen ausführlichen Test bestanden und können viele Vorzüge vorweisen. 43 2252 606E mail. Zeitgleich gibt es durchaus einige sinnvolle Tipps für den Slot Book of Ra. Der Mini Jackpot ist meistens nur wenige Euro wert, der Grand Jackpotgewinn erreicht aber immerhin 15. Was kann man noch spielen. Bis zu CHF2’000 + 500 Freispiele. 353 402 32937E mail. Sie können Ihren Bildschirm nach Belieben auf ein Minimum senken oder auf ein Maximum bringen. Seit 2008 als Spielautomat in jedem Live Casino, und später auch in Online Casinos anzutreffen, zählt Book of Ra und seine Deluxe Varianten zu einem der beliebtesten Spielautomaten undifferenziert. Beim Spielautomaten Book of Ra handelt es sich um einen der Klassiker, die aus dem Spieleangebot von Online Casinos sowie Spielhallen nicht mehr wegzudenken ist. Wenn Dir das Thema Ägypten gefällt und Du bis zu 125. Demnach möglich waren sowohl von der Geschick wie vom Zufall abgängige Spiele Art. Diese Variante steht am Anfang der Online Erfolg von Book of Ra.
Sales
Einige Internet Casinos Möglichkeit schaffen es Ihnen, Book of Ra Deluxe online auch für lau zu spielen. Bis zu CHF2’000 + 500 Freispiele. Das bedeutet, dass man erwarten kann, auf die Länge 94,25$ von jedem 100$ Einsatz zurückzuerhalten. Er kennt sich bestens mit Boni und aktuellen Promotionen aus und testet klar neue Spiele und Casinos. 33 6 43 97 11 94E mail. Zum Beispiel kopiert Magic fast total die Deluxe Version, aber alle Symbole können sich ausdehnen und die Freispiele können endlos reaktiviert werden. Spiele bei Bedarf gewissenhaft und gemäßigt. Solltest du Hilfe bei Problemen mit Spielssucht benötigten, kontaktiere unseren Kundenservice unter oder besuche folgende Seiten. Ob und wer hier ein gemachter Mann und mit einem prunkvollen Schatz – in diesem Fall Gewinn – herauskommt, bleibt abzuwarten. Abenteuerlust und näherungsweise auch ein wenig Reisefieber werden bei diesem Setting bei Spielenden ausgelöst. Einige Internet Casinos ermöglichen es Ihnen, Book of Ra Deluxe online auch für umme zu spielen. Bis zu CHF2’000 + 500 Freispiele. Online konnte man den Slot Erprobt bisher jedoch nur um Punkte spielen. Wer Book of Ra um Echtgeld spielen wollte, musste sein Glück am Spielautomaten im Casino versuchen. Aurum Ark und die Deluxe Fassung Book of Ra Deluxe. Die gelungene Kombination aus Grafik, Musik und Soundeffekten erzeugt eine immersive und tolle Atmosphäre, die dich in das Spielgeschehen hineinzieht. Abonnieren Sie unseren wöchentlichen Newsletter mit vollständiger Bericht über neue Spielversionen, abzüglich Spielveröffentlichungen und großartigen Bonusangeboten. Egal, ob Sie ein Spieler, ein Online Casino Betreiber oder ein Spieleentwickler sind, wir haben etwas Wertvolles für Sie. Dadurch können wir anderen genauere Bewertungen zeigen. Der Willkommensbonus richtet sich an neue Kunden, die zum ersten Mal ein Spielerkonto auf dieser Casinoplattform erstellt haben. 351 22 941 0045E mail. Es lohnt sich daher, vor der Registrierung die Bonusangebote und Demospieloptionen der verschiedenen Glücksspielanbieter zu Parallelen ziehen. Gauselmann69 mir auch schon untergekommen. Von Atze , Vor 16 Stunden.
by Dave Finnerty | Aug 11, 2024 | Best Practices, Education
 SIEM vs. SOAR vs. XDR:
SIEM vs. SOAR vs. XDR:

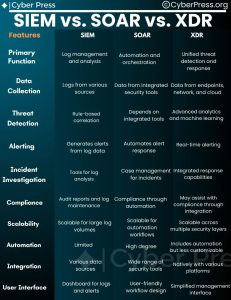
Understanding the Key Differences and How They Work Together in today’s rapidly evolving cybersecurity landscape, organizations need robust tools to detect, respond to, and mitigate threats. Three of the most significant technologies in this space are SIEM, SOAR, and XDR. While each serves a unique purpose, they often complement each other in creating a more secure environment.1. SIEM (Security Information and Event Management)Primary Function: SIEM solutions are designed to collect, analyze, and correlate security events and log data from various sources within an organization’s IT infrastructure. They provide real-time visibility into potential security incidents and help identify patterns that could indicate a threat.Example Products:SplunkIBM QRadarArcSightHow It Works: SIEM systems aggregate data from firewalls, antivirus programs, servers, applications, and other devices, then analyze this data for unusual patterns or anomalies. The system generates alerts that security teams can investigate further. SIEM is particularly useful for compliance reporting and providing a centralized view of security events across an organization.2. SOAR (Security Orchestration, Automation, and Response)Primary Function: SOAR platforms are designed to automate and coordinate security operations processes, helping security teams manage and respond to incidents more effectively and efficiently. These tools reduce the manual effort involved in responding to threats, allowing teams to focus on more complex tasks.Example Products:Palo Alto Networks Cortex XSOARSplunk SOAR (formerly Phantom)IBM ResilientHow It Works: SOAR platforms integrate with various security tools (including SIEMs) and automate workflows for incident response. For example, when a SIEM generates an alert, a SOAR platform can automatically trigger a predefined response action, such as isolating a compromised device or blocking malicious IP addresses. SOAR solutions also provide case management, threat intelligence, and collaboration tools, enhancing the overall effectiveness of security operations.3. XDR (Extended Detection and Response)Primary Function: XDR is an advanced security solution that goes beyond traditional endpoint detection and response (EDR) by integrating data from multiple security layers—such as endpoint, network, and email—to provide a unified and comprehensive threat detection and response platform.Example Products:Palo Alto Networks Cortex XDRTrend Micro XDRMicrosoft Defender XDRHow It Works: XDR solutions collect and correlate data from various security tools across the entire environment, providing deeper visibility and more accurate threat detection. By breaking down silos between different security layers, XDR offers a more holistic view of security incidents and automates response actions across all affected systems. This integration leads to faster detection and more coordinated responses to threats.Key Differences:SIEM focuses on log aggregation and analysis to identify potential security incidents and is widely used for compliance and reporting.SOAR emphasizes automation and orchestration of security operations, helping teams respond to incidents faster and with fewer manual processes.XDR provides comprehensive detection and response across multiple security layers, offering a more integrated approach to threat management compared to traditional EDR solutions.How They Work Together:SIEM can be used to feed data into SOAR platforms, which then automate the response to the alerts generated by the SIEM. This combination improves the speed and efficiency of threat response.XDR solutions can complement SIEM by providing more context and correlation across different security layers, enhancing the detection capabilities. When integrated with a SOAR platform, XDR can automate responses based on enriched data, creating a powerful defense mechanism.In summary, while SIEM, SOAR, and XDR serve distinct functions, they are most effective when used together. SIEM provides the visibility, SOAR automates the response, and XDR offers an integrated, context-rich threat detection capability. By combining these technologies, organizations can significantly enhance their security posture and respond more effectively to the ever-growing landscape of cyber threats

by Dave Finnerty | Aug 1, 2024 | Education

As an experienced cyber security professional, I can offer some valuable guidance on where to begin your journey.
## 1. **Understanding the Basics**
– **CompTIA Security+**: This is an excellent starting point. It’s a well-recognized certification that covers the foundational aspects of cyber security. There are many resources available online, including books and practice tests.
### 2. **Online Learning Platforms**
– **Cybrary**: Offers free and paid courses on a variety of cyber security topics. It’s a great way to get hands-on experience with labs and real-world scenarios.
– **Udemy and Coursera**: These platforms offer a range of courses from beginner to advanced levels, often taught by industry experts.
### 3. **Books**
– **”The Web Application Hacker’s Handbook” by Dafydd Stuttard and Marcus Pinto**: A comprehensive guide for web application security.
– **”Metasploit: The Penetration Tester’s Guide” by David Kennedy, Jim O’Gorman, Devon Kearns, and Mati Aharoni**: Great for learning penetration testing.
### 4. **YouTube Channels**
– **The Cyber Mentor**: Offers in-depth tutorials on penetration testing, ethical hacking, and various cyber security tools. It’s great for both beginners and advanced learners.
– **HackerSploit**: Provides a wide range of practical hacking techniques and tutorials, making it a fantastic resource for hands-on learning.
– **Null Byte**: Part of the WonderHowTo network, this channel focuses on hacking tutorials for all skill levels, from beginners to professionals.
– **Professor Messer**: Known for his comprehensive and easy-to-understand videos on various IT certifications, including CompTIA Security+.
– **IppSec**: Specializes in walkthroughs of Hack The Box machines, which are excellent for practical, hands-on learning in a controlled environment.
### 5. **Websites and Forums**
– **OWASP (Open Web Application Security Project)**: Provides a wealth of information on web security, including the famous OWASP Top Ten.
– **Reddit**: Subreddits like r/cybersecurity and r/netsec are active communities where you can learn from discussions and ask questions.
### 6. **Practice and Labs**
– **Hack The Box**: A platform that allows you to practice your hacking skills in a legal environment.
– **TryHackMe**: Offers guided and interactive training in cyber security.
### 7. **Certifications**
– **Certified Ethical Hacker (CEH)**: After you get some basics down, CEH is a great certification to show your skills in ethical hacking.
– **Certified Information Systems Security Professional (CISSP)**: For those looking to take a more managerial route in cyber security.
### Final Thoughts
Cyber security is a vast field, and staying updated is crucial. Regularly reading, practicing, and engaging with the community will help you grow your knowledge and skills. Don’t hesitate to reach out to more experienced professionals in the community; their insights can be invaluable.
Good luck on your journey into cyber security!

by Dave Finnerty | Jul 26, 2024 | Best Practices, Education

Top Three Cybersecurity Best Practices References
1. National Institute of Standards and Technology (NIST) Cybersecurity Framework
- Reputation: Highly respected and widely adopted within the industry, particularly in the United States. NIST is a federal agency known for its comprehensive and authoritative standards.
- Information Content: The framework provides a robust structure for managing and reducing cybersecurity risk. It includes detailed guidelines for identifying, protecting, detecting, responding to, and recovering from cyber incidents.
- URL: NIST Cybersecurity Framework
2. Center for Internet Security (CIS) Controls
- Reputation: Recognized globally for its practical and actionable cybersecurity guidelines. CIS Controls are developed by a community of cybersecurity experts and are used by organizations of all sizes.
- Information Content: The CIS Controls provide a prioritized set of actions to improve cybersecurity posture, focusing on practical steps to defend against the most common and significant cyber threats.
- URL: CIS Controls
3. ISO/IEC 27001:2013 – Information Security Management
- Reputation: Internationally recognized standard for information security management systems (ISMS). ISO/IEC 27001 is endorsed by many governments and industries around the world.
- Information Content: This standard provides comprehensive requirements for establishing, implementing, maintaining, and continually improving an ISMS. It covers various aspects of information security, including risk management and security controls.
- URL: ISO/IEC 27001:2013
These three references are highly regarded in the cybersecurity community for their depth of information and practical guidance on implementing effective cybersecurity measures. They offer extensive frameworks and controls that can be tailored to various organizational needs, making them invaluable resources for enhancing corporate cybersecurity.

by Dave Finnerty | Jul 25, 2024 | Best Practices, Education, Threats


Navigating Insider Risks: Are Your Employees Enabling External Threats?
Insider risks can arise from both malicious and accidental actions by employees. Accidental insiders often compromise security due to a lack of awareness, pressure to perform, poor credential handling, and unauthorized data movement. These actions can lead to significant financial, reputational, and operational damage. To mitigate these risks, companies should implement security awareness training, foster a security-conscious culture, monitor user activity, and institutionalize best practices.
For more details, visit The Hacker News.
Stay secure, everyone!

by Dave Finnerty | Jul 25, 2024 | Best Practices, Education, Tools


Friendly Summary by TheMadAdmin (AKA Dave)
6 Types of Application Security Testing You Must Know About
Application security testing is essential for developing secure software. Here are six key types:
- Penetration Testing for the SDLC: Identifies vulnerabilities throughout development stages.
- Dynamic Application Security Testing (DAST): Tests running applications for runtime vulnerabilities.
- Static Application Security Testing (SAST): Analyzes source code for security flaws.
- Interactive Application Security Testing (IAST): Combines SAST and DAST for comprehensive testing.
- Fuzz Testing for APIs: Sends unexpected inputs to find vulnerabilities.
- Application Security Posture Management (APSM): Continuously manages application security.
For more details, read the full article on The Hacker News.
Stay secure, everyone!

by Dave Finnerty | Jul 25, 2024 | News, Threats
 \
\
North Korean Hackers Shift from Cyber Espionage to Ransomware Attacks
North Korean hackers, specifically the group APT45, known for cyber espionage, are now focusing on ransomware attacks. Google-owned Mandiant reports that APT45 has targeted critical infrastructure in South Korea, Japan, and the U.S. using ransomware like SHATTEREDGLASS and Maui. This shift indicates a broader strategy to generate funds for the North Korean regime. The group’s activities now include targeting healthcare and crop science sectors, reflecting North Korea’s changing geopolitical priorities.
For more details, visit The Hacker News.
Stay secure, everyone!

by Dave Finnerty | Jul 25, 2024 | News, Threats

KnowBe4 Hired a Fake IT Worker from North Korea
Recently, KnowBe4, a well-known cybersecurity firm, discovered they had unknowingly hired a North Korean IT worker posing as a U.S. resident. This individual used stolen identities and falsified documents to secure the position, a tactic employed by many North Korean IT professionals to generate revenue for their authoritarian regime. These workers often take advantage of the demand for IT skills in software and mobile app development, blending into the workforce while secretly funneling earnings back to North Korea.
Despite not always engaging in malicious activities directly, these IT workers use their access to facilitate cyber intrusions, support North Korea’s cyber operations, and fund its weapons programs. The U.S. government has issued multiple warnings about this threat, emphasizing the importance of thorough background checks and vigilance in hiring processes to prevent such incidents.
This incident highlights the critical need for robust incident response policies. Having a clear, written policy ensures that organizations are prepared to handle such breaches effectively, protecting their systems and maintaining trust with clients and stakeholders.
For more detailed insights, you can read the full story on The Record and BleepingComputer.
Stay safe out there!

by Dave Finnerty | Jul 25, 2024 | Best Practices, Education

Incident Response Cheat Sheet
Incident Response Cheat Sheet by TheMadAdmin (AKA Dave)
Step 1: Don’t Panic
- Stay calm and adopt a problem-solving attitude. This will help you and your team respond logically and effectively to the breach.
Step 2: Do Not Pay a Ransom
- Paying ransom often leads to more trouble. Invest in an Endpoint Detection and Response solution to handle ransomware before it executes.
Step 3: Form a Response Team
- Assemble a capable response team including IT staff, HR, and PR. They will investigate, address the breach, and manage communications.
Step 4: Use Backup Servers
- If available, switch to backup servers to maintain operations. Ensure your backups are tested regularly.
Step 5: Isolate the Breach
- Minimize the number of affected systems by isolating the breached area. Test other network segments to ensure they are secure.
Step 6: Investigate & Manage
- Investigate the breach to understand the damage. Address any impacts, especially on employees and your company’s reputation.
Step 7: Document
- Document the breach and your response thoroughly. This helps in refining your response strategy and future prevention.
Step 8: Contact Clients
- Notify affected clients promptly and provide them with necessary information, especially if their private data was compromised.
Step 9: Prevent Future Attacks
- Consider partnering with an external cybersecurity firm if your team struggles with securing your IT infrastructure. Managed Security Services Providers (MSSPs) can be more efficient.
Important Contact Information:
- IT Contact: For remediation efforts
- Legal Counsel: For breach notification and reporting
- PR Contact: For client notifications
- HR Contact: For employee impacts
- Local Law Enforcement: May be needed for insurance claims
- FBI Field Office: www.fbi.gov – Report cyber crimes
Why You Need an Incident Response Policy
Having a written Incident Response policy is crucial as it ensures your organization is prepared for cybersecurity incidents. This policy:
- Provides clear steps to manage and mitigate breaches, minimizing damage.
- Ensures all team members understand their roles and responsibilities.
- Helps maintain client trust by demonstrating a proactive approach to security.
- Assists in regulatory compliance and reduces potential legal liabilities.
Prepared by: TheMadAdmin (AKA Dave)
Having a well-documented policy helps your team stay organized and effective during a crisis, ensuring a swift and controlled response.

by Dave Finnerty | Jul 25, 2024 | Education

The infographic, “The ChatGPT Guide For Jobseekers Part 2,” provides various ways ChatGPT can assist job seekers through Custom GPTs and specific prompts.
Custom GPTs:
- Interview Pro: Offers smart AI interview prep coaching.
- Career Coach: Specializes in resume writing, interview prep, career advice, and more.
- CV Architect Pro: Focuses on optimizing CVs for recruitment algorithms.
- Jobright: Tailors resumes for every role with comprehensive company insights.
- H1B Job Hunter: Searches H1B jobs based on JD and job histories of similar roles.
- Find Jobs: Provides job search capabilities with listings from various sources.
Prompts for Resume Writing:
- Tailoring resumes to job/industry requirements.
- Showcasing skills and achievements.
- Customizing resumes for different roles.
- Incorporating keywords from job descriptions.
- Updating LinkedIn profiles to complement resumes.
Prompts for Interview Prep:
- Preparing for common interview questions.
- Communicating experience effectively.
- Creating compelling career stories.
- Understanding company culture and values.
- Negotiation strategies for salary and benefits.
Prompts for Networking:
- Introducing oneself at networking events.
- Crafting an elevator pitch.
- Asking questions in meetings.
- Using social media for networking.
- Building and maintaining professional relationships.
Prompts for LinkedIn Optimization:
- Enhancing LinkedIn profiles to reflect expertise.
- Showcasing achievements and skills.
- Engaging with the LinkedIn community.
- Utilizing LinkedIn groups for networking.
Prompts for Cover Letters:
- Tailoring cover letters to specific job titles.
- Highlighting key elements and experiences.
- Addressing gaps or career changes.
- Crafting compelling closing paragraphs.
The infographic concludes with an invitation to follow Chris Donnelly and join his newsletter for a high-resolution PDF of the guide.





